WooCommerce powers millions of online stores worldwide, making it one of the most popular and trusted eCommerce platforms available today. Its flexibility, open-source nature, and seamless integration with WordPress have made it the top choice for businesses of all sizes, from solo entrepreneurs to global retailers. However, with great popularity comes greater risk. Cybercriminals are increasingly targeting WooCommerce store owners through sophisticated phishing attacks designed to steal sensitive data, compromise websites, and disrupt business operations.
In this article, we’ll dive into the latest phishing threats facing WooCommerce users, how to identify fake emails and malicious patches, and most importantly, the proactive steps you can take to protect your store and customers from these growing risks. One essential security measure is blocking IP and email addresses, which can help prevent unauthorized access and reduce fraudulent activity on your site.
In April 2025, a highly deceptive phishing campaign surfaced, specifically targeting WooCommerce users with fraudulent emails masquerading as urgent security alerts. These emails, crafted to look like official notifications, falsely claim a “critical vulnerability” on the recipient’s store and urge them to download a patch. However, this patch secretly contains malware that installs backdoors and jeopardizes the entire business.
The advanced nature of this scam has raised concerns among both store owners and cybersecurity professionals. One WooCommerce merchant even shared their personal experience of receiving such a phishing email:
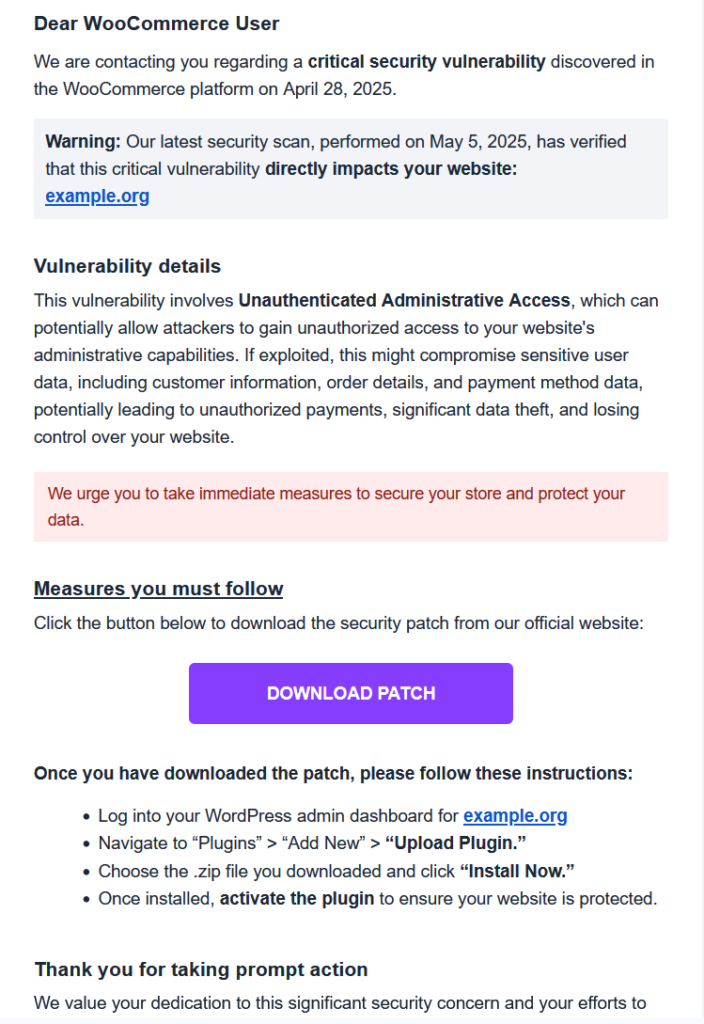
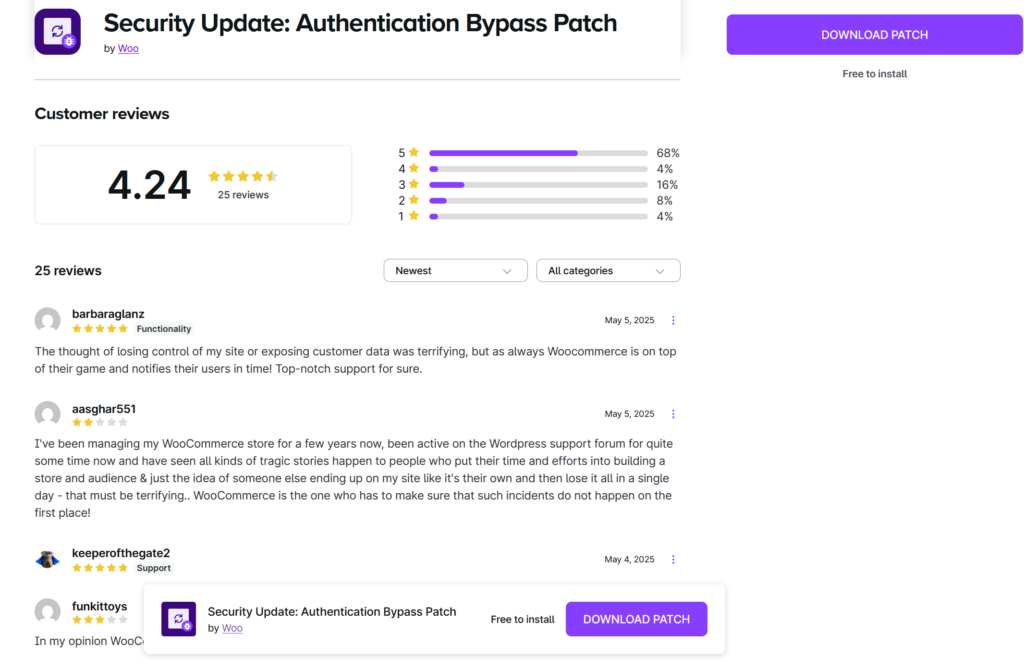
“I just received a phishing email (see image). It looked suspicious, coming from mail-woocommerce.com. I followed the link on a virtual machine, and the page looks almost authentic. They even have fake reviews. I downloaded the proposed ‘patch’, and it’s clearly malicious, with cryptic code. It creates one or more admin users, fetching data from somewhere. The funny thing is that the domain from which they serve the patch is almost identical to woocommerce.com, it’s ‘woocommerċe.com’ with the tiny diacritic on the last ‘c’. On a black on white screen, it could be overlooked as a speck of dust. That is clever, in a twisted, wicked way.”
This striking example highlights just how convincing phishing scams can be—and how easily anyone can be deceived if they’re not paying close attention. With cybercriminals using increasingly sophisticated tactics like homograph domain spoofing, where visually similar characters replace letters to trick the eye, WooCommerce users must remain vigilant, verify sources carefully, and fully understand the threats they face.
In the sections ahead, we’ll break down how this phishing attack operates, teach you how to spot it, guide you on what to do if you’ve been targeted, and share effective strategies to safeguard your WooCommerce store from future attacks.
Inside the Phishing Campaign Targeting WooCommerce Users
In April 2025, security experts uncovered a highly deceptive phishing scam aimed at WooCommerce store owners. The attackers impersonate official WooCommerce messages to spread malware disguised as a “critical security patch,” compromising store security.
How the Scam Operates:
Establishing Persistent Backdoors and Data Theft
Beyond the hidden accounts, the malware installs backdoors — hidden scripts or functions that let attackers access the site remotely at any time. Meanwhile, sensitive customer and store data is quietly transmitted to external servers, risking privacy breaches and regulatory violations.
Deceptive Emails and Domain Spoofing
Store owners receive emails from fake addresses that look official and often mention their real website. The attackers use homograph attacks, registering domains with visually similar letters to fool users into thinking the message is genuine.
Malicious Patch Installation and Site Compromise
The email urges users to download a “security patch,” which is malware. Once installed, it silently creates unauthorized admin accounts, opens backdoors for attackers, and sends sensitive data to remote servers, giving attackers persistent access.
Creation of Hidden Admin Accounts
The malware immediately adds secret admin users to the store’s WordPress backend. These accounts are disguised with names similar to legitimate users or system accounts to avoid detection, allowing attackers to maintain control even if the original malware file is removed.
How to Identify WooCommerce Phishing Emails
Phishing emails are crafted to look like genuine security alerts, but often contain clear signs revealing their fraudulent nature. Here’s how you can spot them:
- Suspicious Sender Addresses
These emails don’t come from official WooCommerce or Automattic domains. Instead, they use misleading email addresses that may seem legitimate at first glance. Examples include:
Although these addresses mention “WooCommerce,” the domains are not owned or managed by WooCommerce. Always verify the domain carefully before taking any action.
- Use of Punycode and Lookalike URLs
Phishing emails often contain links using Punycode, an encoding method that represents special characters in domain names. For example, a fake URL like https://xn--woocommere-7ib.com may appear as woocommerċe.com in browsers.
This subtle difference, such as the tiny dot under the letter “ċ,” can easily be overlooked, especially on smaller screens or mobile devices, tricking users into clicking malicious links.
- Urgent Warnings About Security Vulnerabilities
These fraudulent emails often claim a “critical security vulnerability” exists on your WooCommerce site, sometimes citing a recent date to seem urgent and credible. They frequently personalize the message by referencing your actual store URL, pressuring you to act quickly without verifying the legitimacy of the alert. - Fake Security Patch Downloads
One of the riskiest elements of these emails is the prompt to download a “security patch.” These files are disguised malware designed to compromise your store. Installing them can grant hackers access to your WordPress admin area, expose customer data, and cause lasting damage to your website.
To further safeguard your WooCommerce store, consider implementing strategies for blocking fraudulent customers in WooCommerce — an essential step in preventing malicious activity beyond phishing attacks.
The Hidden Dangers Behind the ‘Download Patch’ Button in WooCommerce Phishing Attacks
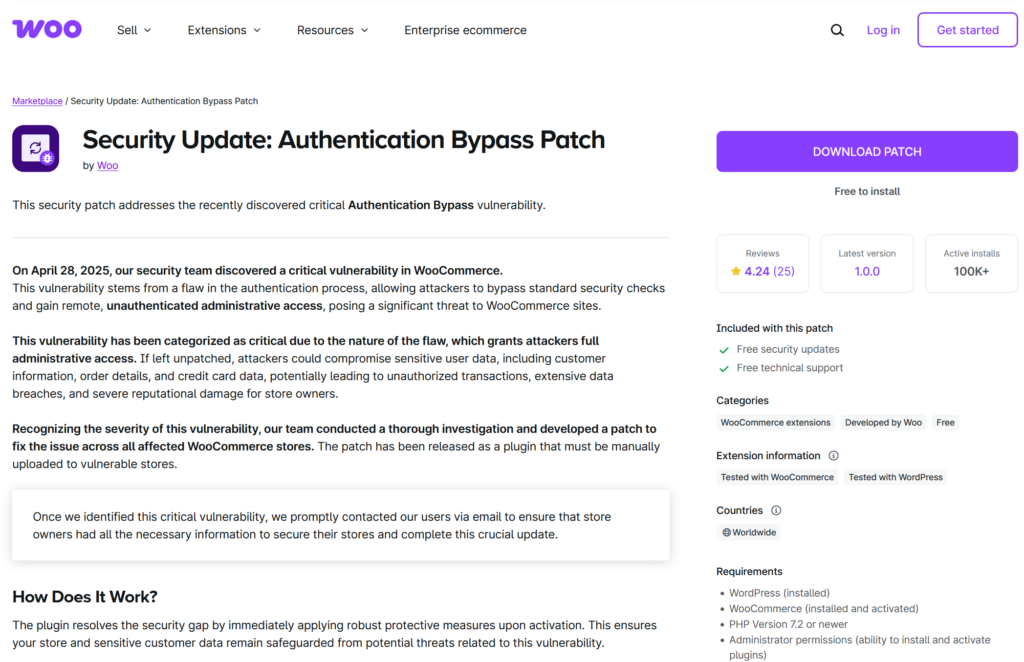
The real threat begins the moment a WooCommerce store owner clicks the fake “Download Patch” link included in a phishing email. What looks like a legitimate plugin or official WooCommerce update is actually a cleverly disguised malware package. Often named something familiar like woocommerce-security-patch.zip, it creates a false sense of trust. However, once installed, it sets off a rapid chain of security breaches.
Step 1: Malware Installation
After uploading and activating the malicious plugin through the WordPress dashboard, the malware executes encrypted or obfuscated code silently in the background. This code is designed to evade standard security scans and inject itself deep within the site’s core files or database.
Step 2: Creation of Unauthorized Admin Accounts
The first major action of the malware is to create hidden admin users. These accounts usually have names that mimic legitimate users or plugins, such as wp-support, admin-helper, or slightly misspelled versions of real usernames, helping them avoid immediate detection.
These backdoor accounts provide attackers with persistent access, even if the original malware file is discovered and removed.
Step 3: Establishing Persistent Backdoors
Next, the malware installs one or more backdoors—hidden scripts or functions allowing the attacker to remotely access the site at will. These backdoors are often disguised as plugin files, theme templates, or cron jobs (scheduled tasks), making them difficult to detect without thorough scanning.
This ensures the attacker can silently regain entry even after cleanup attempts.
Step 4: Exfiltration of Sensitive Data
Once compromised, the site begins transmitting sensitive information, such as customer data, order history, login credentials, and payment details, to external command-and-control servers. This poses serious privacy risks to your customers and may violate data protection laws like GDPR.
Step 5: Further Malicious Exploitation
With full control, attackers can exploit your WooCommerce store in multiple damaging ways, including:
- Sending spam emails using your server resources
- Redirecting customers to counterfeit product pages or scam sites
- Injecting malicious code into your storefront to target visitors
- Deploying ransomware or locking you out of your own admin area
The longer the malware remains active, the greater the financial and reputational damage your store may suffer.
How to Spot Fake WooCommerce Emails
It’s crucial to understand that WooCommerce will never send plugins, updates, or security patches as email attachments or direct download links from unofficial domains.
Official WooCommerce security communications will always:
- Originate from an @woocommerce.com or @automattic.com email address.
- Direct you to trusted websites like WooCommerce.com or WordPress.org.
- Include thorough documentation, clear verification instructions, and transparent details.
If an email deviates from these standards, do not trust it.
What to Do If You Receive a Suspicious Email
If you suspect an email is phishing, take these steps to protect yourself:
- Avoid Clicking Any Links
Don’t click any links—even those that appear legitimate. Phishing emails often hide malicious URLs behind buttons or text designed to look trustworthy. Clicking could lead you to harmful websites or trigger malware downloads. - Do Not Download or Install Any Attachments
Never download or install files sent via email unless you’re absolutely certain of the sender’s identity. These so-called “patches” may:
- Install malware or spyware on your site
- Create unauthorized admin accounts
- Modify your site’s code to open backdoors for attackers
If you have already downloaded such a file, do not open or run it.
- Report the Email as Phishing
Use your email provider’s “Report phishing” feature to flag the message. Most platforms like Gmail and Outlook offer this option. Additionally, you can report suspicious domains to your hosting provider or WooCommerce support to help prevent further attacks.
Protect Your WooCommerce Store: Essential Security Tips
Given the rise in phishing attacks targeting WooCommerce users, here are key steps to keep your store and customers safe:
- Install Updates Only from Trusted Sources
Always update WooCommerce core, plugins, and themes directly from your WordPress dashboard or WooCommerce.com. Avoid installing anything from email attachments or unknown third-party websites, regardless of how convincing the email may look. - Enable Auto-Updates for Security Patches
Many plugin developers, including WooCommerce, regularly release security updates. Activating auto-updates ensures your store stays protected automatically without manual effort, reducing exposure to new vulnerabilities. - Use Strong Passwords and Two-Factor Authentication (2FA)
Protect your admin accounts with strong, unique passwords and enable 2FA. This additional security layer greatly reduces the chance of unauthorized access, even if login details are compromised. - Install Plugins Only from Verified Sources
Download and install extensions exclusively from trusted platforms like WooCommerce.com or WordPress.org. Plugins from unverified sources might contain harmful code or backdoors. - Block Suspicious Activity with Aelia Blacklister for WooCommerce
For extra protection, consider using the Aelia Blacklister for WooCommerce plugin. It lets you automatically block orders or users based on customizable rules, such as:
- Customer name or address
- Email or phone number
- IP addresses or ranges
When a suspicious user is detected, the plugin stops the checkout process and displays a custom message, helping to prevent repeat fraud attempts and reduce potential security threats.
